Memory acquisition is usually the first step in digital forensics analysis. Before any analysis can be done, we need to acquire the memory in
the first place. There are a number of commercial solutions to acquire memory, but there is also a few free and even open source equivalents.
In this article I am going to review four memory acquisition utilities designed to deploy on a USB stick for quick incident response
operations.
Basic requirements:
- free of charge
- minimal memory footprint
- portable (no installation required) and lightweight
- x86 and x64 support
All tools were tested on my Windows7 x64 machine with 8GB of RAM. Let’s get started!
Magnet RAM Capture
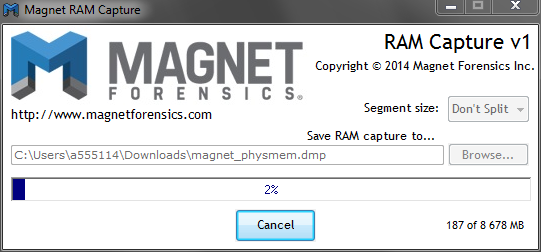
Magnet RAM Capture is a new player in the market. Supports Windows systems including XP, Vista, 7, 8, 10, 2003, 2008, and 2012. Magnet RAM
Capture has nice and simple GUI so running it is very straightforward. It creates a raw memory dump with a .DMP extension. If you are running
the tool from a FAT32 formatted USB stick and the host RAM you are capturing is greater than 4 GB, then segmentation feature will be very
helpful (it is disabled by default).
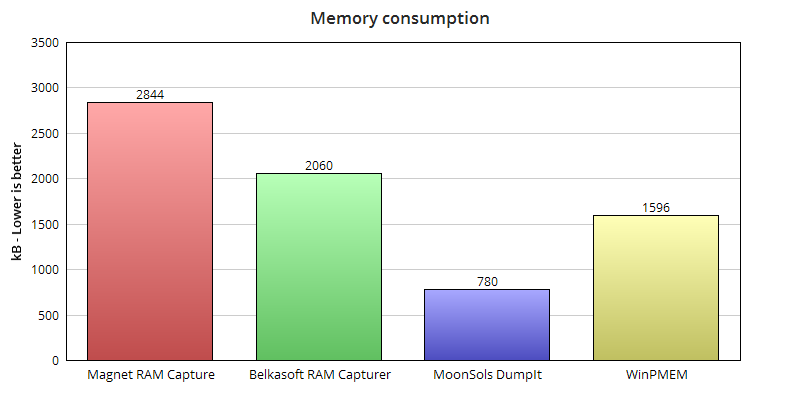
During my tests, Magnet RAM Capture allocated 2844K of memory.
Belkasoft Live RAM Capturer
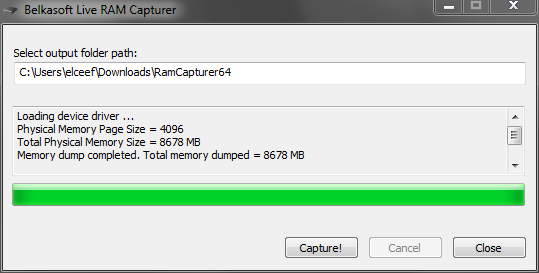
Belkasoft Live RAM Capturer is compatible with all versions and editions of Windows including XP, Vista, Windows 7 and 8, 2003 and 2008
Server. The authors claim that they did their best to optimize memory usage. It is even available in separate 32-bit and 64-bit versions in
order to minimize it’s footprint as much as possible. The tool comes equipped with kernel drivers allowing it to operate in the most
privileged kernel mode. Thanks to GUI it is very simple to use. By default it stores memory image in current working directory. It creates a
memory dump in RAW format. The name of the output file is the current system date with .MEM extension.
During my tests, 64-bit version of RAM Capturer allocated 2060K of memory.
MoonSols DumpIt
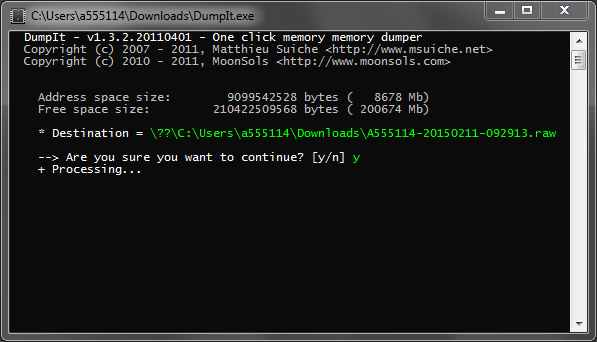
MoonSols DumpIt is a fusion of old win32dd and win64dd combined into new and improved executable. It is also part of MoonSols Windows Memory
Toolkit. DumpIt offers an easy way of obtaining a memory image even if the investigator is not physically sitting in front of the target
system. It is designed to be provided to a non-technical user. Only a double click on the executable and confirmation is enough to generate a
copy of the physical memory in the current directory. A .RAW memory image named for the host name, date and UTC time will result.
Unfortunately free of charge version I used (1.3.2.20110401) is a few years old and is not developed any more. There is also commercial version available with LZNT1 compression and RC4 encryption features, but of course it is not free and therefore does not meet our basic requirements.
During my tests, DumpIt allocated only 780K of memory. Great result.
Rekall WinPMEM
WinPMEM is actively developed open source utility. It is part of Rekall Memory Framework. WinPMEM has never let me down. It acquired 64GB memory image from Windows 2008 Server. Compared to the previously described tools, WinPMEM has a number of interesting features:
- output formats: RAW memory images and ELF Core dump files
- output to STDOUT for piping through other tools like ssh, netcat, 7zip
- memory acquisition using four different methods
- optional write support for manipulating kernel data structures through
\\.\pmemdevice
WinPMEM is slightly harder to use. It can be run only from command line which makes it ideal for scripting purposes. Your script can be deployed on a USB stick and do the job for you. My personal favourite feature is writing images to standard output (STDOUT). For example, you can use it to transfer memory image directly to a remote machine:
winpmem_1.6.2.exe - | nc 10.0.0.1 1234
Or to create a password protected archive on the fly:
winpmem_1.6.2.exe - | 7z a -si -bd -pSECRET
During my tests, WinPMEM allocated 1596K of memory. You need to remember that in combination with other tools like nc or 7z, memory consumption will be higher.
Memory consumption comparison
Well, the chart speaks for itself.